Do you use social media or other digital venues to share your art and creative works? As an influencer, your online presence and reputation is valuable, so it’s important to take steps to protect yourself from malicious actors. We’ve grown wary of the huge number of intrusive digital threats ruling and have had to adapt so the safety of our online presence is not compromised.
In this article, you’ll find out what we learned about some of the more common digital threats for influencers, and how you can protect yourself from them.

Key Learning Objectives:
- Understand the different types of digital threats and how they can affect influencers
- Learn tips to help protect yourself from malicious actors who target influencers
- Types of digital threats: There are many different types of digital threats out there, from trolls and cyberbullying to identity theft and malicious software
- How to prevent and overcome digital intrusion into your personal digital space
Introduction
It’s no secret that your online presence and reputation are important to maintain as an influencer. With the increasing number of digital platforms, it has become easier than ever for malicious actors to target influencers.
It is critical that you take steps to protect yourself from these threats by implementing proper security measures and staying vigilant in monitoring your online activity.
Why Digital Safeguards?
What’s wrong with my existing security? Most computer operating systems nowadays include their own security measures in case of a malicious attack. However, these can sometimes be insufficient as many cyber-criminals are able to find loopholes and exploit them for their own gain.
This can be especially problematic if you rely on your digital presence for income, a livelihood, or even to maintain your reputation for yourself or your business.
We’ve even written about the signs of when you’re ready to turn your hobby into a business. Taking the extra steps to add further safeguards to your digital presence can help protect you from malicious actors and keep your data safe.
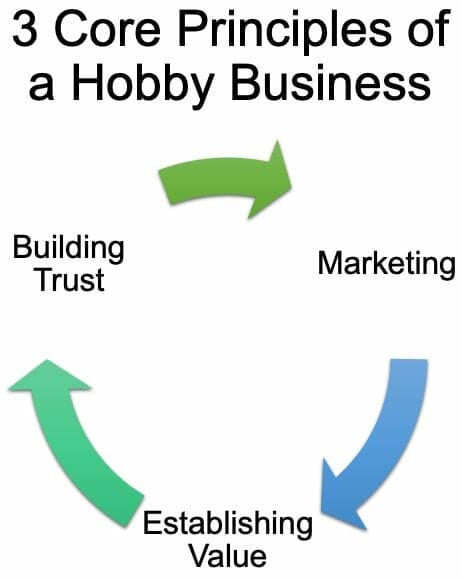
While it is unnerving to say, even the smallest breach in your online workspace can be costly. They can easily drive a fledgling business into the ground.
Here, we’re going to look at a host of online threats, how they can endanger your digital presence e.g., business, social media sites, and what actions you can take to protect yourself.
Phishing Scams
Social engineering attacks work by tricking members of your team, leading to them exposing vulnerabilities. The most common type is the phishing email, in which a team member receives a scam email and follows a link or downloads an attachment that contains a threat.

It’s vital to provide thorough cybersecurity awareness training and to establish protocols for evaluating the validity of emails and messages they receive. By doing so, you can help make sure your team is less likely to fall for threats like these.
The simplest solution to avoiding phishing scams is to delete any email that looks suspicious and to never click on links or download attachments from unknown senders.
DDoS Attacks
Distributed denial of service attacks or DDoS attacks is a type of malicious cyber-attack that attempts to disrupt the normal operations of a particular computer system or network by overwhelming it with high levels of internet traffic.

Incoming fake traffic or overloading your server host will stop or delay legitimate users and employees from accessing your online assets.
As you can imagine, the goal of these attacks is to make the target system(s) unavailable for your audience, usually by flooding it with so many requests that the network is unable to respond. This can cause significant damage to an organization’s reputation, finances, and even customer trust.
If you’re wondering if this kind of attack is possible on social media sites, such as Facebook, Instagram, Twitter, then the answer is yes. DDoS attacks can be launched against any type of online platform.
How to you prevent a DDOS attack? To protect your network from these attacks, it’s important to stay up to date on blacklisted IPs and prevent them from accessing your network.
For bloggers or web masters, it’s important to take steps to protect your websites and networks from these attacks by using web application firewalls or other suitable security measures.
Some host providers have additional features to help protect against DDOs, so it’s important to do your due diligence and research any provider you choose.
Ransomware
Ransomware is a type of malicious software, or malware, that encrypts the data on a victim’s computer and then demands payment in order to unlock it. It can be spread through phishing emails, fake downloads, malicious websites, and other methods. Once ransomware penetrates a system, it usually takes control over the user’s files, locking them until a ransom payment is made.

In the past, companies have had to pay as much as $1 million to ransomware hackers to regain access to their data. Globally, ransomware attacks may account for over $20 billion in lost revenue.
Ransomware attacks are on the rise (occurring nearly once every 11 seconds to online entities), and they can cause serious damage to businesses or individuals who don’t have backups of their data.
It’s important to keep your systems updated with the latest security patches and be aware of phishing emails or suspicious websites that could be used to spread ransomware.
In addition, it’s critical to run regular backups of your important files and store them offsite, as this can help you restore lost data in the event of an attack. Finally, be sure to install reliable anti-virus software that will help protect against ransomware attacks.
Fileless malware
Malware is a type of software that’s designed to harm your computer or steal your data. It can be spread through infected email attachments, malicious websites, and other methods.
Many malware threats, like the ransomware mentioned above, require you to download files to your device in order to be affected by them. However, there is some malware that requires no such thing but makes use of vulnerabilities in existing programs.
Also known as “fileless malware”, these threats don’t require a file to be installed on the victim’s computer in order to execute its payload. Instead, it uses built-in system tools or PowerShell scripts to execute its code and achieve its goals.
Fileless malware can be very difficult to detect, as it doesn’t leave any traditional indicators of infection. To learn how to protect against fileless malware, keeping your existing software up to date is vital. It’s also important to have strong anti-virus software installed on your computer and keep it up-to-date, as well as maintain good internet security practices.
Attacks from the inside
Do you trust your team? Your employees or even volunteers? It’s important to remember that not all of the threats you face come from outside your organization.

Sometimes, the biggest security threat comes from within. For big companies, celebrity influencers, and even the small business, insider threats can be a major problem.
Insider threats come from individuals already inside your organization who have access to sensitive information and use it maliciously or for personal gain.
It could be an employee sharing confidential data with an outside party, a volunteer stealing customer data, or even a disgruntled former employee exploiting security vulnerabilities.
To protect against these threats, it’s essential to oversee your data access controls and make sure that no one has access to data that isn’t necessary for their responsibilities.
Additionally, it’s crucial to remove access privileges from anyone who leaves the company or organization to prevent them from potentially accessing sensitive data.
For the influencer working alone, you should realize that there are many digital support systems that you rely on. Each of these are potential targets and should be carefully monitored and secured as best you can.
Protecting your data is just as important when you are working alone as it is when you have a team of people that rely on it.
Other Potential Threats to Your Online Presence
Although we’ve listed the major threats above with potential ways to prevent security breaches to an online business or influencer presence, there are many other potential dangers in cyberspace.
It would be impossible to cover them all in a reasonable amount of time, but here are a few that should be mentioned:
- Social media bots (e.g., could contribute to DDoS attacks)
- Hackers
- Phishing scams (very common)
- Identity theft
- Credit card fraud
- Malware and ransomware (see above)
- Data breaches (internal or external)
- Cyberbullying (i.e., could include doxing)
- Unsolicited emails
- Spam websites and links
- Online scams
- Weak passwords
- Unsecured Wi-Fi networks
- Viruses on personal devices
- Fake online profiles and accounts
The key to preventing problems is always having a vigilant outlook on what you do in the online space. It’s also important to know who you’re engaging with, what links and websites you or your audience are accessing, and always use secure passwords that can’t easily be guessed.
Of course, make sure to regularly update your software and keep the latest security protocols in place for the best protection against online threats.
For this site, we are very careful to audit every outgoing link we publish to ensure security is maintained for our readers.
Our Experience with a Security Threat
We’ve been the target of a phishing scams for years. The most recent one was at the beginning of this year when we got an email from a seemingly legitimate source (who was on our email newsletter list) asking us to resend a digital 3D file from our store.
One member of our team was asked to transfer the file through a disguised FTP (file transfer protocol) link, but that set off alarms. ⚠️

Fortunately, our team was able to identify the threat/scam before any damage could be done. We quickly reported the incident and blocked the URL from all of our systems.
After that, we took a few extra precautionary measures: we updated our security settings, ran scans on our system for any potential weak spots, and reminded all staff of the importance of spotting the signs of malicious attacks.
In the end, we were able to identify and prevent this attack before it caused any harm. But it’s a reminder of how important it is to stay vigilant when it comes to cybersecurity threats and to take steps to protect your data.
Final Word
I hope you found this article helpful and a reminder of the importance of understanding and protecting against cyber threats.
We all need to be aware of the risks out there so we can best protect ourselves and our data. Remember, it’s your responsibility to do everything you can to keep yourself and your information secure.
Although we’re primarily a hobby focused blog, we know that security is an essential part of the online community we maintain, and would love to keep the conversation going.
If you have any comments, thoughts, or feedback about this emerging topic in the influencer and other online business spaces, we’d love to hear from you.
Thanks for stopping by! Until next time, stay safe out there.






Tangible Day on YouTube (Miniatures and More!)

